Blogs
A Successful DISC Training Event with Sierra Collins
Monday night, we had the pleasure of attending a DISC training session led by Sierra Collins at the Renaissance Events Center in Shippensburg. The event, held in the beautiful venue owned by Jonathan Bohannon, was a fantastic evening of learning and personal growth....
Expanding Wireless Infrastructure in Challenging Environments
At iWAT LLC, we pride ourselves on our ability to support and facilitate the expansion of our clients' technological infrastructure, regardless of the size or complexity of the project. Recently, we undertook a significant challenge that perfectly exemplifies our...
iWAT LLC Wins Property Improvement Award: Contributing to a Better Chambersburg
At iWAT LLC, we are honored to announce that we have received a Property Improvement Award from the Cumberland Valley Business Alliance (CVBA). This award recognizes our commitment to enhancing the community of Chambersburg through significant improvements to our...
Virtualization Project
Our company recently acquired 192 Cores, 768 GB of memory from AMD for our next project!!!! With multiple cores, these processors enable efficient multitasking and enhance overall system performance. The substantial memory capacity is crucial for virtualization...
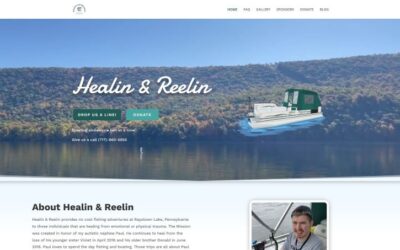
Healin & Reelin
As a charitable organization that provides no-cost fishing adventures to those healing from emotional or physical trauma, Healin and Reelin needed a website that would not only showcase their mission but also make it easy for people to learn more and get involved. Our...
Protecting Your Digital Footprint
In today's fast-paced, interconnected world, where digital technologies permeate every aspect of our lives, the importance of cybersecurity cannot be overstated. With the ever-evolving threat landscape and the potential for catastrophic consequences, individuals and...
Why EDR is Essential for Modern Cybersecurity
EDR, or endpoint detection and response, is a type of cybersecurity technology that helps protect computer systems and networks from threats. It is important because it can detect and respond to potential threats in real-time, helping to prevent data breaches and...
Ransomware
Has your business been hit by ransomware? Ransomware is one of the most worrying cyber threats with a huge potential for damage. The sad part is that this type of malware is on the rise. The ever-evolving technology and the...
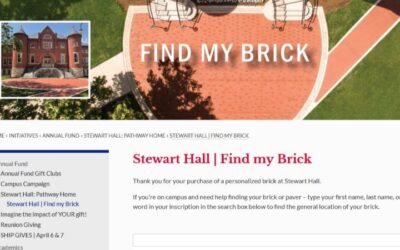
Brick Finder
What Is Brick Finder? Brick Finder is a PHP and JS WordPress plugin designed to support the restoration of the Stewart Hall at Shippensburg University. The plugin was developed for the Shippensburg University Foundation specifically for their restoration efforts....
Most Common IT Issues
Many common IT problems can be solved without the assistance of an IT professional but sometimes you do need to call in extra help. Some of these issues include but are not limited to:Blue Screen of DeathPrinter ProblemsFailure to Recognize a USB DeviceLogin...
Is a Wired Connection Superior to Wi-Fi?
We live in a wireless world where most people embrace the convenience of Wi-Fi connection at home and in the workplace. Wi-Fi offers the ease and flexibility to download, stream or browse as long as the user is within the range of an access point. With these benefits,...
Pros and Cons of Upgrading to Windows 11
Pros and Cons of Upgrading to Windows 11 Microsoft officially began its rollout process for Windows 11 on 5th October, and it's gradually phasing out Windows 10. The tech giant has reported that Windows 10 support will end in October 2025, meaning you still...
Lets Encrypt Takes Over The SSL Market
The free SSL service Lets Encrypt now has over 50% of the SSL market, and overall adoption has increased significantly. This news is not too surprising since in 2014 Google said it would give ranking precedence to SSL encrypted sites over non-SSL encrypted sites. This...
Our Solutions
Our professionals combine proven services and capabilities to enable lasting business transformation with sustained results.